Large amounts of data from a Chinese cybersecurity company have been leaked online, showing its contracts and communications with the Chinese government for collecting important digital information at home and abroad — including in countries such as India, Nigeria, Indonesia and the United Kingdom.
Data Leak From A Chinese Cybersecurity Agency
Why In News
- Large amounts of data from a Chinese cybersecurity company have been leaked online, showing its contracts and communications with the Chinese government for collecting important digital information at home and abroad — including in countries such as India, Nigeria, Indonesia and the United Kingdom.
- I-Soon, a Shanghai-based company (also transliterated from the Mandarin as Auxun), is believed to be one of the many private contractors that help the Chinese state conduct its intelligence-gathering, hacking and other surveillance activities. Last week, 190 megabytes of information were posted on the software and code-sharing platform GitHub.
What’s In The Leaked Data
- The data trove shared on GitHub contains emails, images, conversations and a trove of documents. According to a report in The Washington Post, they “detail contracts to extract foreign data over eight years and describe targets within at least 20 foreign governments and territories, including India, Hong Kong, Thailand, South Korea, the United Kingdom, Taiwan and Malaysia”.
- These documents do not contain the actual information that was secured. But they have details about the targets of the surveillance, and the contracts that were awarded to I-Soon.
- “One spreadsheet listed 80 overseas targets that iSoon hackers appeared to have successfully breached,” the report said.
- This included “95.2 gigabytes of immigration data from India and a 3 terabyte collection of call logs from South Korea’s LG U Plus telecom provider”. Also, “459GB of road-mapping data from Taiwan, the island of 23 million that China claims as its territory,” was listed, according to The Post report.
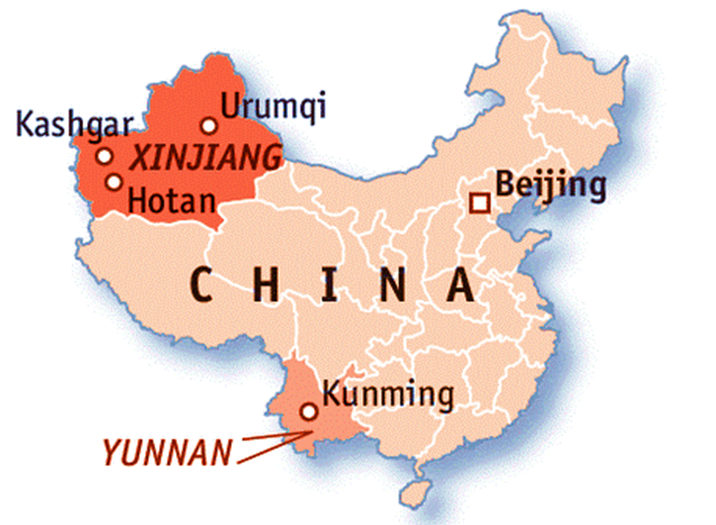
- Within China, the targets seemed to include “ethnicities and dissidents in parts of China that have seen significant anti-government protests, such as Hong Kong or the heavily Muslim region of Xinjiang in China’s far west”, the Associated Press reported.
Indian Targets
- The leaked data mentions Indian targets like the Ministry of Finance, the Ministry of External Affairs, and the “Presidential Ministry of the Interior”, which likely refers to the Ministry of Home Affairs.
- The advanced persistent threat (APT) or hacker groups retrieved 5.49GB of data relating to various offices of the “Presidential Ministry of the Interior” between May 2021 and October 2021, at the height of India-China border tensions.
- “In India, the main work targets are the ministry of foreign affairs, ministry of finance, and other relevant departments. We continue to track this area in depth and can tap its value in the long term,” reads the translated India section of what appears to be an internal report prepared by iSoon.
- User data of state-run pension fund manager, the Employees’ Provident Fund Organisation (EPFO), state telecom operator Bharat Sanchar Nigam Limited (BSNL), and private healthcare chain Apollo Hospitals were also allegedly breached. Air India’s stolen data pertains to details of daily check-in by passengers.
- The list of targets ranged from then President Ram Nath Kovind and Prime Minister Narendra Modi to Congress leader Sonia Gandhi and their families; then Chief Ministers Ashok Gehlot, Amarinder Singh, and Uddhav Thackeray; Cabinet Ministers Rajnath Singh, Nirmala Sitharaman, Smriti Irani, and Piyush Goyal; the late Chief of Defence Staff Bipin Rawat and at least 15 former Chiefs of the Army, Navy, and Air Force; then Chief Justice of India Sharad A Bobde; and top industrialists Ratan Tata and Gautam Adani.
- About 95GB of India’s immigration details from 2020, described as “entry and exit points data”, were also referred to in the leaked documents. Notably, 2020 saw an escalation in India-China relations following the Galwan Valley clash.
- “India has always been a huge focus of the Chinese APT side of things. The stolen data naturally includes quite a few organisations from India, including Apollo Hospital, people coming in and out of the country in 2020, the Prime Minister’s Office, and population records,” Taiwanese researcher Azaka, who first highlighted the GitHub leak.
- John Hultquist, the chief analyst at Google Cloud-owned Mandiant Intelligence, was quoted by the Washington Post saying the online dump was “authentic data of a contractor supporting global and domestic cyber espionage operations out of China”. “We rarely get such unfettered access to the inner workings of any intelligence operation,” he said.
Other Targets
- Apart from India, Beijing also allegedly targeted its “all-weather friend” Pakistan. Other apparent targets include Nepal, Myanmar, Mongolia, Malaysia, Afghanistan, France, Thailand, Kazakhstan, Turkiye, Cambodia, and the Philippines, among others.
- As per the leaked dataset, as much as 1.43GB of postal service data from the “Anti-Terrorism Centre” in Pakistan’s Punjab province was obtained by the Chinese hacker group between May 2021 and January 2022. The documents also indicate that the Chinese government sanctioned snooping on Pakistan’s Ministry of Foreign Affairs and telecommunication company Zong.
- Huge amounts of data were also allegedly stolen from Nepal Telecom, Mongolia’s Parliament and police departments, a French university, and Kazakhstan’s pension managing authority. The hackers also allegedly accessed the official systems of the Tibetan government-in-exile and its domain, Tibet.
- For years, hacking groups linked to China’s Communist Party, like Mustang Panda or APT41, have been running malicious campaigns, targeting organisations and countries including the US to gather intelligence. The US recently launched an operation to fight a pervasive Chinese hacking operation that compromised thousands of internet-connected devices.
- This isn’t the first time China has been in the spotlight for cyber attacks in India. In 2022, China-linked hackers reportedly targeted seven Indian power hubs. Threat actors attempted to get into India’s power infrastructure in 2021 as well.
- 20th ASEAN-India Summit & 18th East Asia Summit Highlights
- Manipur Police Register Criminal Case Against Assam Rifles
- Pakistan’s Ex-PM Imran Khan Jailed For 3 Years In ‘Toshakhana Case’
- Four Years After Removal Of Art 370: How Is The Actual Situation In Kashmir?
- Putin’s Critic Alexei Navalny Sentenced To 19 More Years In Prison
- Delhi Services Bill Tabled In Lok Sabha: Govt Of NCT Of Delhi (Amendment) Act, 2023
- Gurugram Nuh Violence: How A Religious Procession Turned Into A Communal Clash
- Govt Imposes Import Restrictions On Laptops, Tablets, Computers
- How Climate Change Is Altering The Colour Of The Oceans?
- New IPCC Assessment Cycle Begins: Why Is It So Significant?
- Difference Between NATO Vs Russia? [Explained]
- Italy Regrets Joining China Belt & Road Initiative (BRI)
- What Is Doping: Why Is It Banned In Sports?
- India Tiger Census 2023: India Is Now Home To 75% Of Tigers In The World
- Military Coup In Niger – President Detained, All Institutions Suspended
- No-Confidence Motion Against PM Modi’s Government
- Elon Musk’s SpaceX Rocket Punches Hole In Ionosphere
- Israeli Parliament Passes Controversial Law Stripping Supreme Court Of Power
- Significance Of 1999 Kargil War: How It Became A Major Game Changer For Indian Military?
- Controversy Over Movie Oppenheimer Gita Scene: How Are Films Certified In India?
- The Curious Case Of Qin Gang: China’s Foreign Minister Who Went Missing
- Twitter’s Iconic Blue Bird Logo Set To Be Replaced By An X Logo
- India Pulls Out Of Games In China Over Stapled Visas For Arunachal Athletes
- PM Modi Urges Sri Lanka President To Implement 13th Amendment
- India Pulls Out Of Games In China Over Stapled Visas For Arunachal Athletes
- Rajasthan CM Sacks Minister After Remarks Over Crimes Against Rajasthan Women
- Manipur Sexual Assault: Video Sparks Outrage Across The Country
- BRICS Summit 2023 In August: Why Putin Won’t Go To South Africa For The Summit?
- Robert Oppenheimer: The Father Of Atomic Bomb, Impact Of Bhagavad Gita On Him
- Russia-Ukraine Black Sea Grain Deal, Why Russia Has Halted It?
- Henley Passport Index 2023, India Passport Ranked 80th
- Indian Opposition Parties Form ‘INDIA’ Alliance, 26 Parties Unite For 2024
- Britain Joins Asia-Pacific Trade Group ‘CPTPP’ – Biggest Trade Deal Since UK Left EU
- NITI Aayog Report On National Multidimensional Poverty Index
- PM Modi UAE Visit: Highlights & Key Takeaways
- PM Modi’s Visit To France: Highlights & Key Takeaways
- NATO Summit Vilnius 2023: Highlights & Key Takeaways
- Turkey Supports Sweden’s Bid For NATO Membership At Vilnius Summit 2023
- Why ISRO Wants To Explore The Moon’s South Pole: Chandrayaan-3 Mission
- Bengal’s Panchayat Polls Turned Violent: SSB Interview Topic 2023
- First Ever IIT Campus Outside India In Tanzania
- RBI’s Report On “Internationalisation Of Rupee” Why And What Are The Benefits?
- Japan To Release Nuclear Wastewater Into Ocean – Gets Approval From IAEA
- PM Modi Chairs 23rd SCO Summit: Highlights & Key Takeaways
- Israel Raids Jenin Camp: Massive Military Operation In West Bank
- Dutch King Apologizes For Netherlands’ Role In Slavery: A Look At The Dutch Role In History
- Constitutional Crisis In Tamil Nadu: The Tussle Between Governor & DMK Government
- Why Has France Been Engulfed By Protests Again?
- Paris Summit – World Leaders Unite For A New Global Financing Pact
- India Ranked 67th On Energy Transition Index – Sweden On Top Of List By World Economic Forum
- Four Minor Planets Named After Indian Scientists
- NASA Recovers 98% Water From Urine & Sweat On ISS: Breakthrough In Long Space Missions
- ESA Space Telescope Euclid Is All Set For Launch To Observe Dark Side Of Universe
- PM Modi’s Trip To USA: Key Takeaways & Highlights
- PM Modi-Led Yoga Session Creates A New Guinness World Record
- Sajid Mir, The Mastermind Behind 26/11 – His Designation As Global Terrorist Blocked By China
- UN Adopts First Historic ‘High Seas Treaty’ To Protect Marine Life
- International Yoga Day 2023 – How It Was Celebrated Across The World?
- Gender Apartheid – Why Is Afghanistan At Stand Off With UN?
- Gandhi Peace Prize 2021 For Gita Press Why It Triggered A Congress-BJP Brawl?
- The New Pride Flag – Why The Change & What The Colours Signify?
- 48 Years Of Emergency – PM Modi Refers It As India’s Darkest Period In Mann Ki Baat
- Groundwater Extraction Has Tilted Earth’s Spin – How Will It Impact The Climate Change?
- Europe’s Worst Migrant Boat Disaster – 78 Dead, Hundreds Missing Off Greek Coast
- MOVEit Global Hacking Attack – Government Agencies In The USA Targeted
- Karnataka Govt Decides To Repeal Anti-Conversion Law: Why Was The Law Controversial?
- IIT Bombay Among Top 150 Varsities In QS Rankings 2024
- China’s Xi Jinping Backs ‘Just Cause’ Of Palestinian Statehood – Chinese Middle Eastern Diplomacy
- Turkey Won’t Back Sweden’s Bid To Join NATO – Why Is Erdogan Against Sweden’s Application
- UN Report Reveals Chronic Bias Against Women – 25% Of Population Thinks Beating Wife Justifiable
- Zinnai – Space Flower Grown On International Space Station By NASA – Why Is It Significant?
- Who Are Meira Paibis: Manipur’s ‘Torch-Bearing’ Women Activists?
- USA Set To Re-Join UN Cultural Agency UNESCO
- CoWIN Data Leak – Aadhaar, PAN Card Info, On Covid Portal, Made Public By Telegram
- $10bn Investment Deals Signed At Arab-China Summit – Is Arab World Moving Towards China?
- Cyclone Biparjoy Turns Into Extremely Severe Cyclonic Storm – 10 Points To Know
- PM Modi’s Trip To Egypt: Highlights & Key Takeaways
- El Nino Returns After 7 Years: Will Impact Second Half Of Monsoon
- Europe’s Copernicus Programme Completes 25 Years: SSB Interview Topic
- Trump Charged Over Secret Documents In A First For An Ex-US President
- 39 Years Since Operation Bluestar: What Actually Happened?
- Wagner Chief Vows To Topple Russian Military Leaders
- Arctic Could Be Ice-Free In The Summer By 2030: SSB Interview Topic
- PM Modi’s School In Gujarat Will Host Students From Across India
- Major Dam Collapse In Ukraine – Accuses Russia Of Blowing Up Kakhovka Dam
- Microsoft To Pay $20 Million For Illegally Collecting Children’s Info
- NIRF Ranking 2023: IIT Madras Tops The List For 5th Consecutive Year
- TRAI’s ‘Digital Consent Acquisition’ (DCA) Facility’- Unified Platform For Customers’ Consent
- 34th Anniversary Of Tiananmen Square Protest – Hong Kong Police Detains Activists
- Asia Security Summit 2023 Shangri-La Dialogue Begins Amid China-US Tensions
- Coromandel Express Accident – How 3 Trains Derailed, Crashed At Same Place In Odisha
- Law Commission Against Scrapping Of Sedition Law, Says It Will Protect India’s Unity
- Radical Changes In NCERT Textbooks – Poverty, Inequality, Democracy Among Topics Removed
- India GDP Data Beats Expectations – Stays Fastest Growing Economy
- Maharashtra’s Ahmednagar To Be Renamed Ahilyanagar
- Scientists Discover 2nd Moon Near Earth Orbiting Since 100 BC
- Erdogan’s Victory In Turkish Election – What Can Be The Impact On India?
- NASA Alert! GIANT Asteroid Racing Towards Earth
- Uganda Signs Anti-Gay Law With Death Penalty – Sparks Global Outrage
- RBI’s ‘Lightweight’ Payments System For Emergencies – An Alternative To UPI, NEFT, RTGS
- Significance Of ISRO’s Newly Launched NavIC Satellite In Regional Navigation
- What Is The Model Prisons Act – Reforms In The Indian Prisons System?
- Global Plastic Treaty – Negotiations Underway For A Plastic-Free Planet: SSB Interview Topic
- China Sends First Civilian Astronaut To Space As Shenzhou-16 Blasts Off
- US Congressional Panel Suggests Making India Part Of NATO Plus: SSB Interview Topic
- India Conducts National Cyber Defence Exercise
- What Is XPoSat, India’s First Polarimetry Mission?
- Germany Falls Into Recession As Inflation Hits Economy
- Bangladesh Faces Fuel Crisis – Dollar Shortage Issue
- Australian Universities Ban Student Applications From Certain Indian States
- What Is Volt Typhoon: China-Backed Hackers Targeting USA?
- Death Of Six Cheetahs At Kuno National Park: SSB Interview Topic 2023
- India-Australia Relations Get Stronger – What Is Migration Deal?
- What Is Sengol: To Be Placed In The New Parliament Building?
- Annual Misery Index – India Ranks 103 Out Of 157 Nations: SSB Interview Topic
- Russia Pressures India For Help To Avoid Getting Blacklisted By FATF
- What Is Mission LiFE – How It Will Fight Against Climate Change?
- What Is The ‘Pandemic Treaty’: How WHO Could Fight Future Pandemics?
- Assam CM Himanta Biswa Sarma Announces Withdrawal Of AFSPA
- El Nino Could Hit World Economy By $3 Trillion? SSB Interview Topic 2023
- Tussle Between Delhi Govt And Centre – Delhi Ordinance Issue: SSB Interview Topic
- China Braces For New Covid Wave With Up To 65 Million Weekly Cases
- Colour-Coded Warnings By The IMD: SSB Interview Topic 2023
- Saudi Scripts History As First Arab Woman Astronaut Lifts Off Into Space
- Controversy Behind Inauguration Of Parliament Building: SSB Interview GD Topic
- Uniform Civil Code: Is Time Ripe For the Indian Government To Act On It?
- Indian-Origin Ajay Banga To Be The Next World Bank President
- AI ‘Godfather’ Geoffrey Hinton Quits Google Warns Of Danger Ahead
- India Ranks 161 Out Of 180 Countries – World Press Freedom Index
- Supreme Court Rules It Can Directly Grant Divorce To Couples: SSB Interview GD Topic
- Kashmir All Set To Hold G20 Summit In India
- Go First Airlines Files For Insolvency: SSB GD Topic
- India Becomes Europe’s Largest Supplier Of Refined Fuels
- What Is The Met Gala – Fashion’s Biggest Night?
- Clashes In France Against Pension Reforms By Macron Govt
- Why Are Indian Wrestlers Protesting Against WFI Chief?
- China Offers Ukraine To Mediate To End War With Russia
- 50 Years Of Kesavananda Bharati Case: SSB Interview Lecturette Topic
- Assam-Arunachal Pradesh Border Dispute: SSB Interview Lecturette Topic 2023
- Same-Sex Marriages In India: Key Supreme Court Verdicts On LGBTQ Rights
- What Is China Plus One? SSB Interview Lecturette Topic 2023
- India-Maldives Relations: SSB Interview Lecturette Topic 2023
- India-Bangladesh Relations: SSB Interview Lecturette Topic 2023
- India-Japan Relation: SSB Interview Lecturette Topic 2023
- Geopolitical Importance Of The Indian Ocean: SSB Interview Lecturette Topic 2023
- All About Paris Club: SSB Interview Lecturette Topic
- PM Narendra Modi Has Been Named The Most Popular Leader In The World
- Hindenburg Report On Adani – Here’s What You Need To Know
- India At WEF Davos Summit 2023: Here Are 10 Key Highlights
- Pakistan Economic Crisis 2023: SSB Interview Topic [Fully Explained]
- Joshimath Crisis: What Does “Land Subsidence” Mean, And Why Does It Happen?
- Top 10 Animal Conservation Projects In India [MUST WATCH]
- What Is Shanghai Cooperation Organisation (SCO) Summit 2022? [Fully Explained]
- 20 SSB Interview Questions On Russia Ukraine Crisis
- What Is The (India-Israel-UAE-USA) I2U2 Summit? [Fully Explained]
- What Is International North-South Transport Corridor (INSTC)?
- What Is Sri Lankan Crisis? [Fully Explained]
- What Is The BIMSTEC Grouping And How Is It Significant? [EXPLAINED]
- What Is The Places Of Worship (Special Provisions) Act, 1991? [Explained]
- What Is Bodo Accord | SSB Interview Notes [Fully Explained]
- What Is AFSPA: Armed Forces (Special Powers) Act?
- What Is G20 Or Group Of Twenty Countries?
- What Is AFSPA: Armed Forces (Special Powers) Act?
- What Is The Financial Action Task Force (FATF)? [Fully Explained]
- What Is Quadrilateral Security Dialogue (QUAD)?
- Difference Between NATO Vs Russia [Expained]
- What Is United Nations Security Council (UNSC) [Explained]
- Everything You Need To Know About SAARC: South Asian Association For Regional Cooperation
- All About Russia Ukraine War: SSB Interview Topic [Fully Explained]